
China's Cyber Spies Take to High Seas as Hack Attacks Spike
- October 15, 2015
- Southeast Asian nations more vulnerable to cyber attack
- China-U.S. pact only covers theft of corporate secrets
In the midst of a weeklong hearing on a South China Sea territorial dispute, the website of the Permanent Court of Arbitration in The Hague went offline.
The incident happened in July as the Philippines challenged China’s claim to more than 80 percent of the South China Sea, an assertion that Manila says encroaches on its exclusive economic zone. Based on an analysis of the software and infrastructure used, the site was infected with malware by someone in China, according to ThreatConnect Inc., a U.S. security company. China didn’t take part in the Hague hearing.
Alongside the increased presence of coastguard and military ships and planes, cyber espionage is emerging as a new front in the wrangling over the South China Sea, an artery for global trade that straddles the Indian and Pacific oceans. Over the past 18 months China has rapidly built on reefs in the area, butting up against smaller claimants such as Vietnam and the Philippines.
China regularly uses its coast-guard and even fishing vessels towarn away the boats of other countries. The disputes have pulled in the U.S., which patrols the waters in the name of navigational freedom -- most recently it has reportedly been considering sailing warships into the 12 nautical mile exclusion zone around the islands China is building.
“Whenever you see island-dispute issues flare up you also see cyber activities spike as well,” said Tobias Feakin, director of the International Cyber Policy Centre at the Australian Strategic Policy Institute in Canberra. “If it is being used in coordination with the prodding that the Chinese do in a physical way, it surely shows you see a strategic advantage in the use of that power.”
Dated Networks
The smaller economies of Southeast Asia are vulnerable to hacks, given a lack of spending on cyber defense by some countries that rely on remittances from thousands of their citizens working overseas to propel growth, and a reluctance to report breaches of government security. The one protection may be how dated or incomplete networks are, with a reliance in far-flung areas on paper files.
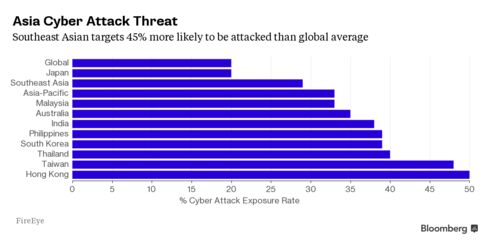
Southeast Asian governments and companies are 45 percent more likely to be targeted than the average for the rest of the world, security provider FireEye Inc. said in a recent report. While President Xi Jinping agreed last month with President Barack Obama to broad principles to stop the theft of corporate secrets, the yet-to-be-developed rules will only cover the U.S. and China and won’t extend to traditional intelligence collection.
“The Chinese aren’t going to shut down their cyber-espionage operations,” said Dmitri Alperovitch, co-founder and chief technology officer of security company CrowdStrike Inc. “So they are most likely going to double down on traditional intelligence collection.”
In The Hague, the Philippines was seeking to enlist international law to deter China’s expansion in the South China Sea. Hackers embedded the PCA’s web page on the case with code that infected visitors to the page, according to ThreatConnect. That left diplomats, lawyers and journalists interested in the case at risk of information theft, plus their wider organizations.
‘Big Net’
“It’s like catching fish with a net,” said ThreatConnect Chief Intelligence Officer Rich Barger. “I dip a big net into the ocean, I collect fish over the course of a few hours, and then I have the option of pulling out a few targeted fish that I wanted to have. ”
The PCA website was unavailable for a short period in July due to technical problems, Gaelle Chevalier, a case manager at the PCA, said via e-mail, adding “we have no information about the cause of the problems.” Philippine President Benigno Aquino’s deputy spokesperson Abigail Valte, who was at The Hague, said she heard about the attack. “We were surprised.”
There are other signs of cyber attacks on countries at times of tension with China. When China dragged an exploration oil riginto contested waters last year, it led to deadly anti-China protests in Vietnam and clashes at sea between coast guard boats. There was a spike in cyber attacks on Vietnamese government targets, according to CrowdStrike.
Peaceful Purposes
Neither the Chinese foreign ministry nor the defense ministry responded to faxed questions about alleged Chinese involvement in the breach of the PCA or Vietnamese government websites. Officials regularly claim China is a victim of cyber security breaches and have repeatedly denied being the source of hacks of the U.S. and other countries. The foreign ministry contends its island-building program in the South China Sea is legitimate because the reefs are its sovereign territory, and that the construction is for peaceful purposes.
Vietnam has seen a rise in cyber attacks on government sites with more than 3,000 defacement attacks and over 5,000 malware attacks in the first half of the year, according to the information security authority in the Ministry of Information and Communications. Hackers were found to have used Internet protocol addresses based in countries including China, the U.S. and Russia, it said in an e-mailed response to questions.
Vital Events
“Whenever there has been a vital political, economic or social event, such as when the South China Sea disputes get heightened and complicated, attacks on government agency websites, especially those with a domain of .gov.vn, were seen to rise in volume, scope and mode,” the authority said.
CrowdStrike’s claims jibe with those of FireEye, whose Mandiant division alleged in February 2013 that China’s military may be behind a group that hacked at least 141 companies worldwide since 2006. After the report was published, the U.S. issued indictments against five military officials who were alleged members of that group, known as Advanced Persistent Threat 1.
In April, FireEye identified a group named APT 30 it said had spent a decade targeting governments, the military and corporations in Southeast Asia. It said software code and language were among indicators the software used in attacks was developed in China.
Also worrying was the ability of the group to successfully breach its targets despite barely having to upgrade its tools, tactics, and infrastructure over the years, according to Bryce Boland, FireEye’s Singapore-based Asia-Pacific chief technology officer.
“APT30 has been operating for 10 years and they didn’t even need to change the servers they were using,” said Boland. “They didn’t need to lift a finger to obfuscate where they were coming from.”
ThreatConnect has identified a group of hackers called Naikon APT which it says is backed by the People’s Liberation Army. Known as unit 78020, the group conducts cyber-espionage against Southeast Asian targets, ThreatConnect and Defense Group Inc. wrote in a report published last month.
While China is viewed as the most active of the region’s cyber-espionage actors, other countries are developing capabilities, according to CrowdStrike’s Alperovitch. “But the Chinese have been in this game for 15 years so they are head and shoulders above everyone else.”
No comments:
Post a Comment
Comments always welcome!